How HTTPS Works: Securing Data Transmission on the Web
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP.) HTTPS transmits encrypted data using Transport Layer Security (TLS.) If the data is hijacked online, all the hijacker gets is binary code.
How is the data encrypted and decrypted?
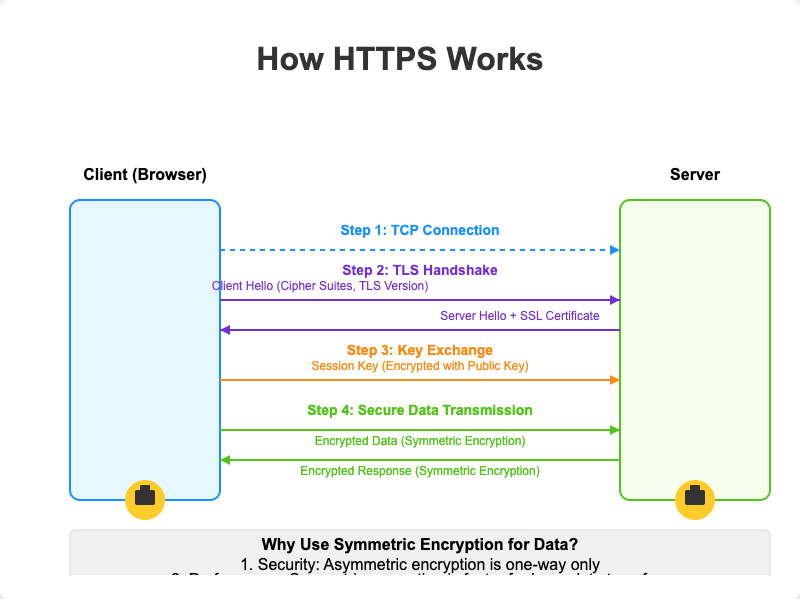
The client (browser) and the server establish a TCP connection. This is the foundation upon which the secure connection will be built.
The client sends a “client hello” to the server. The message contains a set of necessary encryption algorithms (cipher suites) and the latest TLS version it can support. The server responds with a “server hello” so the browser knows whether it can support the algorithms and TLS version.
The server then sends the SSL certificate to the client. The certificate contains the public key, host name, expiry dates, etc. The client validates the certificate.
After validating the SSL certificate, the client generates a session key and encrypts it using the public key. The server receives the encrypted session key and decrypts it with the private key.
Now that both the client and the server hold the same session key (symmetric encryption), the encrypted data is transmitted in a secure bi-directional channel.
Why does HTTPS switch to symmetric encryption during data transmission? There are two main reasons:
Security: The asymmetric encryption goes only one way. This means that if the server tries to send the encrypted data back to the client, anyone can decrypt the data using the public key.
Performance: The asymmetric encryption adds quite a lot of mathematical overhead. It is not suitable for data transmissions in long sessions.
HTTPS provides several important benefits:
You can easily identify if a website is using HTTPS by looking at:
HTTPS has become the standard for secure web communication, protecting sensitive information like login credentials, payment details, and personal data. Understanding how it works helps appreciate the complex security mechanisms that keep our online activities safe.
The next time you see that padlock icon in your browser, you’ll know exactly what’s happening behind the scenes to protect your data!